- Home
- About Pixie
- Installing Pixie
- Using Pixie
- Tutorials
- Reference
Pixie allows you to connect multiple Kubernetes clusters to a single Pixie Cloud instance. The main advantage of such a deployment is that you can monitor all your Kubernetes clusters from a single point.
This guide explains how to share a Pixie Cloud instance across multiple Pixie deployments.
- A domain name that you own
- Prerequisites of the install method your choice; Self-hosted Pixie or Air Gapped Pixie
Install the NGINX Ingress Controller in your Kubernetes cluster. Please refer to the NGINX Ingress Controller Installation Guide for more information.
Note the IP address assigned to the Ingress Controller service. All requests to the Pixie Cloud will be sent through this.
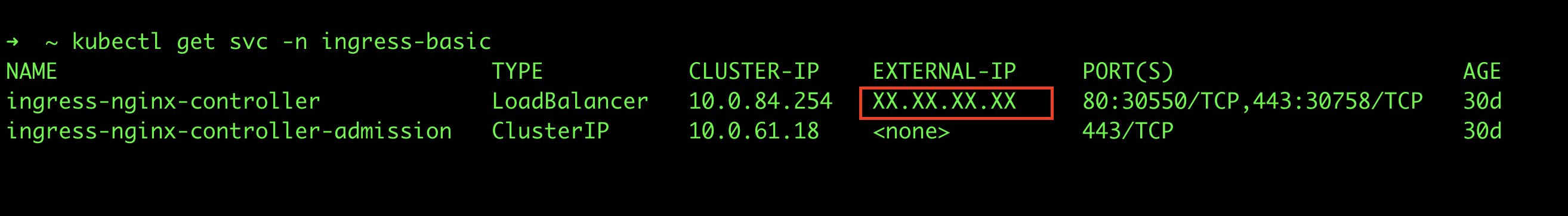
E.g. The following image shows the services created in the namespace where the NGINX Ingress Controller was installed. Note the IP address in the EXTERNAL-IP column of the ingress-nginx-controller Load Balancer service.
Two DNS A records need to be created pointing to the NGINX Ingress controller IP address obtained above.
Suppose that your Pixie custom domain name is pixie.example.com and the IP address obtained above is a.b.c.d. Two A records need to be created as follows.
pixie.example.com a.b.c.dwork.pixie.example.com a.b.c.d
If you are using the Self-Hosted installation,
- Follow steps 1 - 5 and 8 in Deploy Pixie Cloud.
- Comment lines 94 to 106 in
./scripts/create_cloud_secrets.sh - Execute the script as explained in step 9 of Deploy Pixie Cloud
If you are using the Air Gapped installation,
- Follow steps 1 and 4 in Deploy Pixie Cloud
- Comment lines 94 to 106 in
./scripts/create_cloud_secrets.sh - Execute the script as explained in step 6 of Deploy Pixie Cloud
A TLS certificate is required for the custom domains that you wish to use with Pixie.
Suppose that your Pixie custom domain name is pixie.example.com. You need to obtain a single certificate that is valid for both pixie.example.com and work.pixie.example.com. Finally, create a Kubernetes secret (of type kubernetes.io/tls) named cloud-proxy-tls-certs in the plc namespace using the certificate.
One way to obtain it is by creating a Let's Encrypt certificate using cert-manager. Securing NGINX-ingress tutorial from cert-manager has detailed information about the process.
Here are sample resources that can be used with cert-manager:
Sample ClusterIssuer resource
apiVersion: cert-manager.io/v1kind: ClusterIssuermetadata:name: letsencrypt-cluster-issuerspec:acme:server: https://acme-v02.api.letsencrypt.org/directoryemail: admin@example.comprivateKeySecretRef:name: letsencrypt-cluster-issuer-keysolvers:- http01:ingress:class: nginx
Sample Certificate resource
apiVersion: cert-manager.io/v1kind: Certificatemetadata:name: cloud-proxy-tls-certsnamespace: plcspec:dnsNames:- pixie.example.com- work.pixie.example.comsecretName: cloud-proxy-tls-certsissuerRef:name: letsencrypt-cluster-issuerkind: ClusterIssuer
Two Kubernetes Ingresses are required for Pixie Cloud; One for HTTPs and the other for gRPCs communication.
Create two ingresses as follows.
kubectl apply -f k8s/cloud/overlays/exposed_services_nginx/cloud_ingress_grpcs.yamlkubectl apply -f k8s/cloud/overlays/exposed_services_nginx/cloud_ingress_https.yaml
If you are using the Self-Hosted installation,
- In
k8s/cloud/public/domain_config.yamlset the value ofPASSTHROUGH_PROXY_PORTto be empty.
PASSTHROUGH_PROXY_PORT: ""
- Complete steps 10 - 13 in Deploy Pixie cloud
- Skip the Set up DNS section
- Complete the steps in Authentication using Kratos / Hydra
- (Optional) - Complete the steps in Invite others to your organization (optional)
- Install the Pixie CLI as explained in Install the Pixie CLI
If you are using the Air Gapped installation,
- Complete steps 7 - 11 in Deploy Pixie Cloud
- In
yamls/cloud.yaml, find the ConfigMap namedpl-domain-config. Set the value ofPASSTHROUGH_PROXY_PORTin it to be empty.
PASSTHROUGH_PROXY_PORT: ""
- Complete the remaining steps (from step 12 onwards) in Deploy Pixie Cloud
- Skip the Set up DNS section
- Complete the steps in Authentication using Kratos / Hydra
- Complete the steps in Serve the Script Bundle
- (Optional) - Complete the steps in Invite others to your organization (optional)
Finally, deploy Pixie in each cluster that you wish to monitor.
If you are using the Self-Hosted installation, in Deploy Pixie instructions, skip the --dev_cloud_namespace plc flag when executing px deploy commands.
If you are using the Air Gapped installation, deploy Pixie as explained here.